Compliance on AWS refers to adhering to regulatory and industry standards while using Amazon Web Services for secure and compliant cloud computing. According to the AWS documentation, AWS Config is an offering that streamlines managing configuration compliance on AWS.
Configuration and relationships between resources on AWS, on-premises, and other clouds can be continuously assessed, audited, and evaluated using AWS Config.
Note:
In order to determine the price of AWS Config, you need to know the configuration item, and rule you are creating
Problem statement
If an EC2 instance is associated with a public IP address, it can be accessed over the internet despite protections like NACLs or security groups. To reduce the risk of unauthorized access, avoid public IP associations except when essential. Same goes for the S3 buckets and its objects, as they should not be accessible to the public internet directly atall. For example, CloudFront is a highly secure, and reliable offering used to deliver content of a website hosted on an S3 without the making the object publicly accessible. click on content delivery with cloudfront to see the article i wrote on how to do this.
This post outlines the process of performing a compliance check on EC2, and S3 using AWS Config. AWS-managed Configuration service rules was used to check compliance on an EC2 instance and S3 bucket.
Here is our architecture overview:
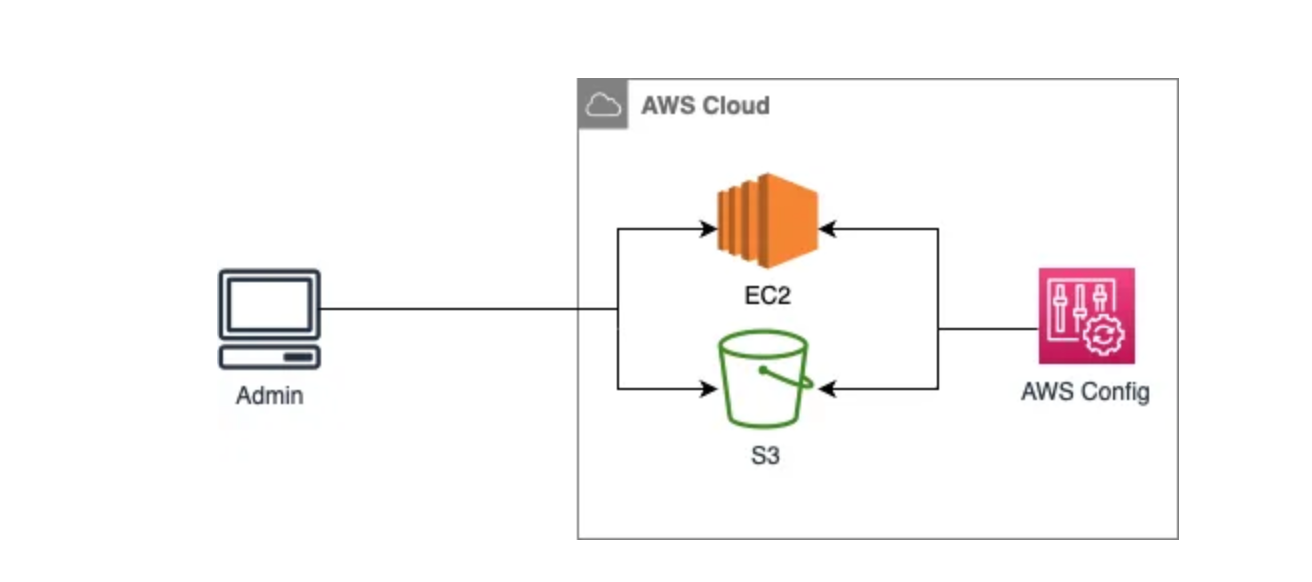
Prerequisites
EC2 instance: you will need to launch or have an instance running. Getting started with EC2 outline steps on how to launch an EC2
S3 bucket: you will need to create an S3 bucket for this demo. Click Getting started with S3 bucket to see guide on how to create one.
Screenshots of EC2 and S3 bucket below.
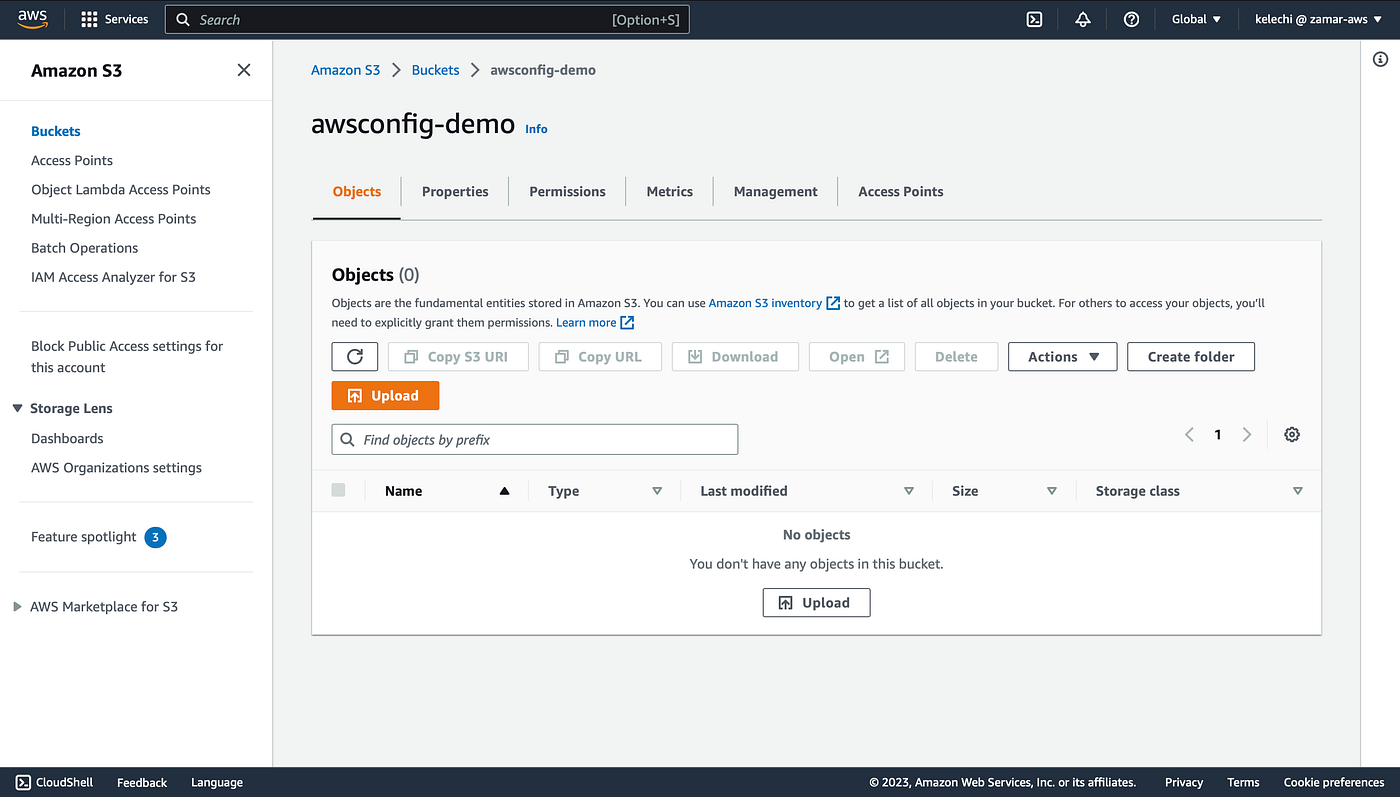
S3 bucket
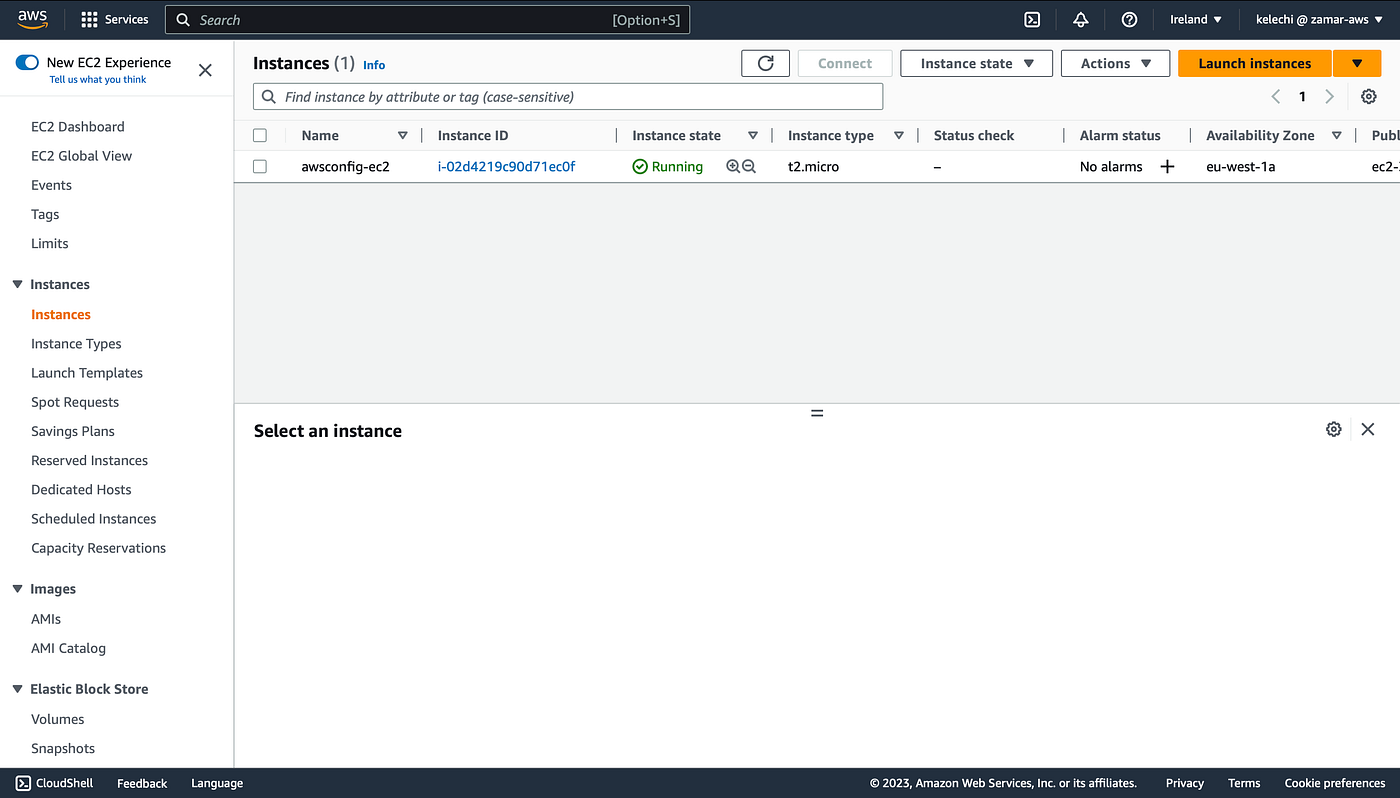
EC2
To check compliance for EC2 and S3, follow the below steps:
Access the AWS Config console and add an AWS-managed rule.
Then, view the resource inventory to see compliant and noncompliant resources.
Fix configuration issues of the AWS resources — EC2 and S3 bucket
View the resource inventory to see review compliance
A. Now lets create our rule on AWS Config
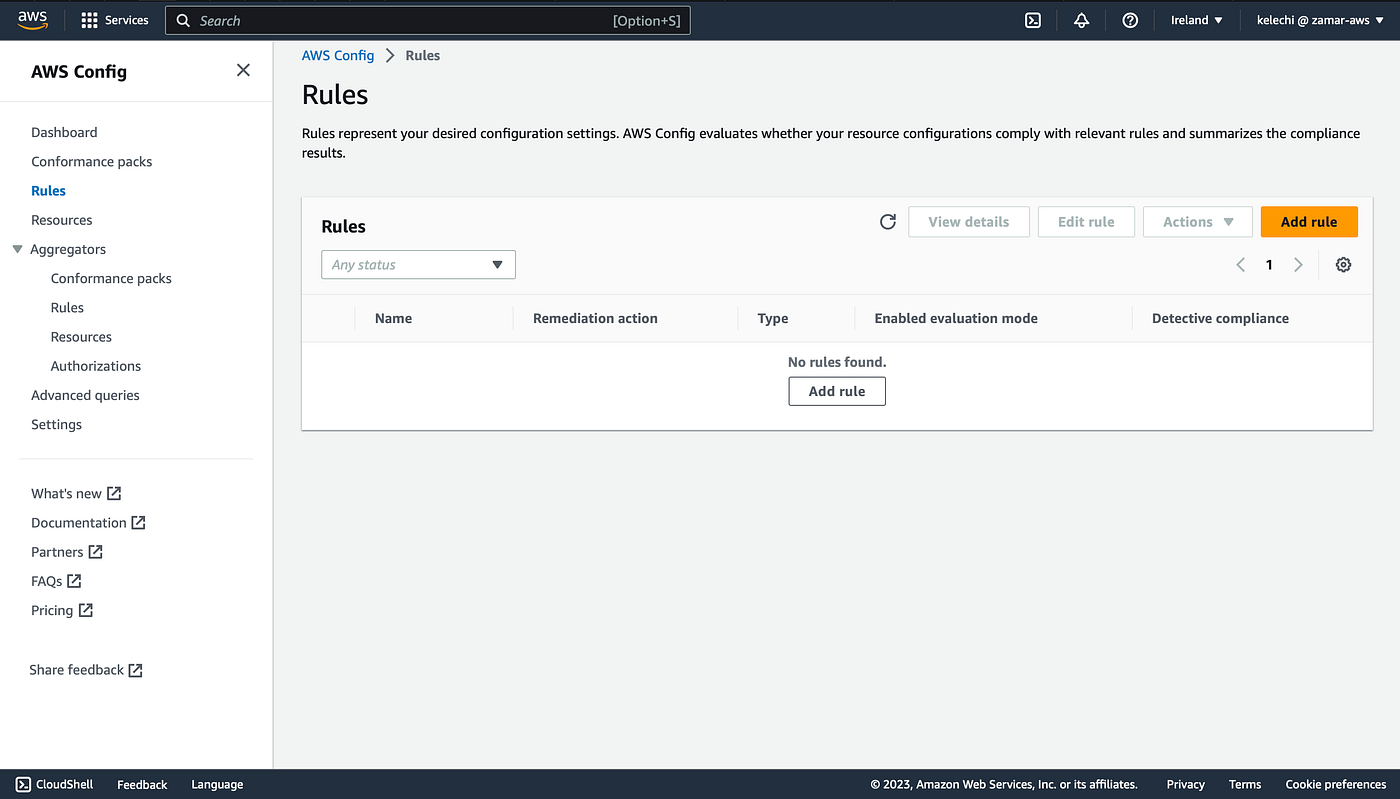
No rules created yet
i. Create a rule to check compliance for public IP association for the EC2 instance.

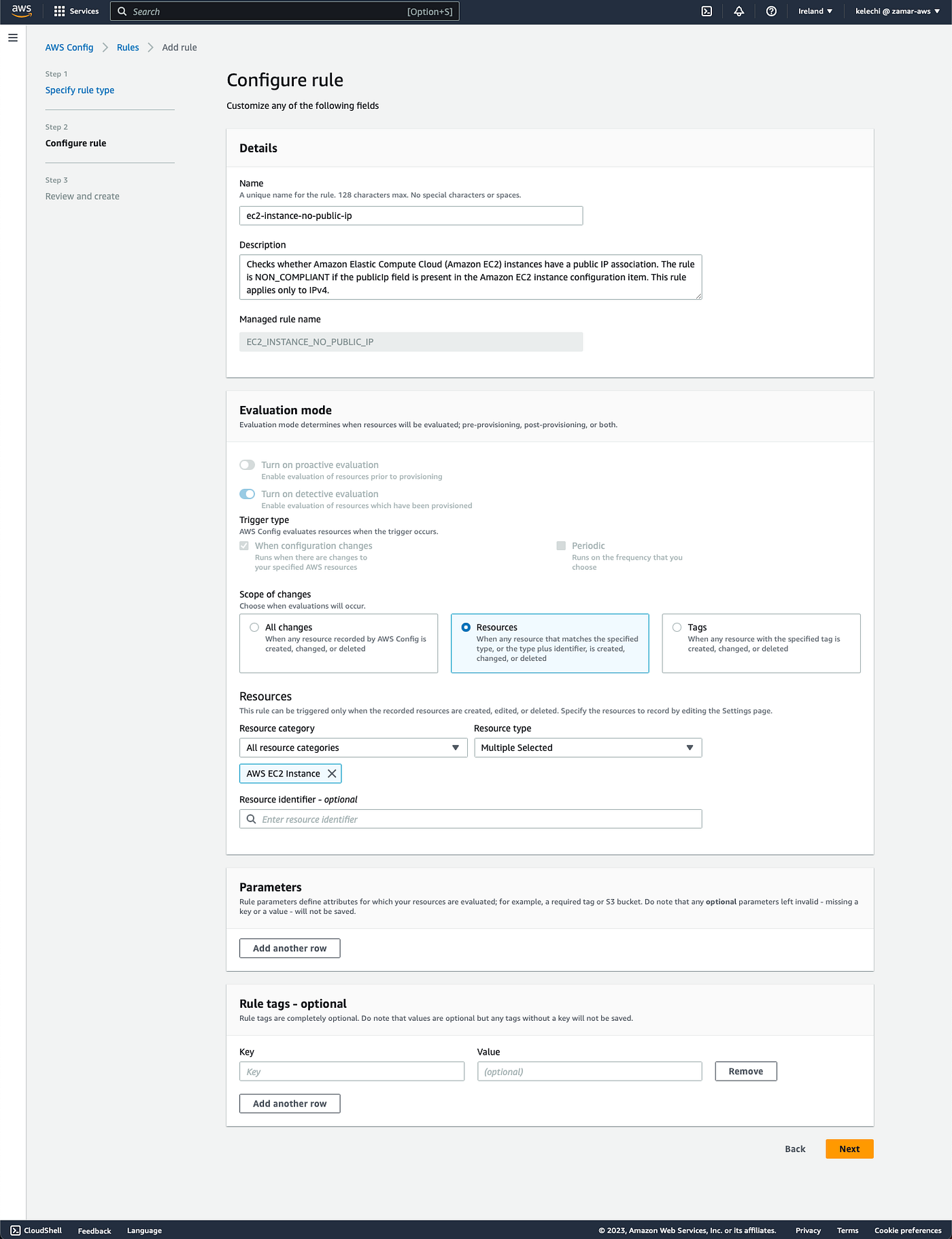
ii. Create a rule to check block public access for S3 bucket. An S3 bucket will be considered non-compliant if it allows public access to its objects.



Created rules

Rules page
From the above image, we can already see we have noncompliant resources, hence we need to fix their configurations to make them compliant.
B. Let us review the resource inventory to view compliance on resouces.

Resource Inventory — Showing non-compliant resources
The resource inventory is used to view the compliance status of AWS resources being monitored by AWS Config. It provides detailed information on the resources and their configurations, allowing users to identify noncompliant resources and take action to fix configuration issues, ensuring compliance with regulatory and industry standards.
As seen in the above, the EC2 instance and the S3 buckets are noncompliant.
C. We proceed to fix configuration issues of the AWS resources — EC2 and S3 bucket.
i. We turn on the ‘Block public access (bucket settings)’ feature by selecting the checkbox as seen in the image below, then click on save changes.

ii. We have removed the public ip from our running instance. There are alternative steps to ensure your ec2 instances do not have a public ip addresses in this website.
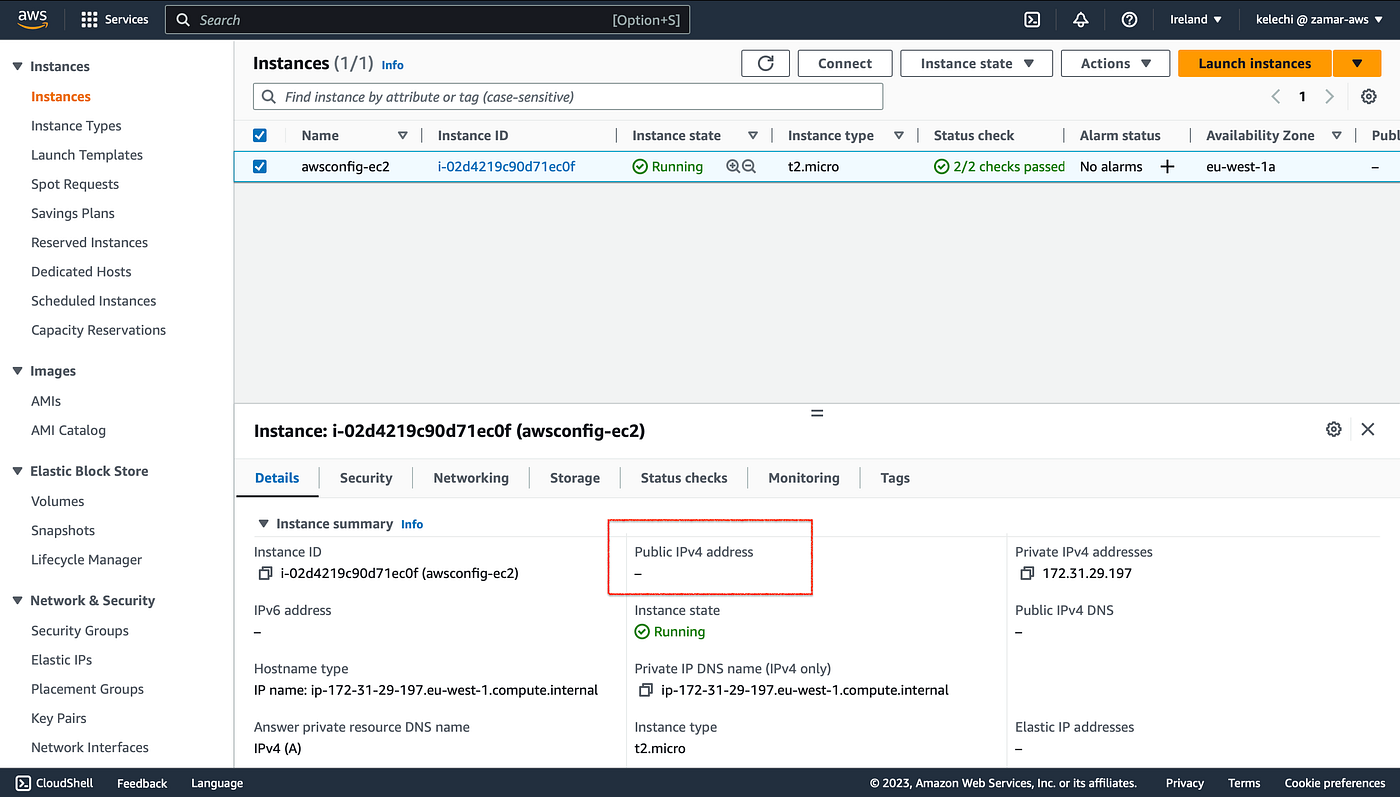
EC2 Instance — no Public IP address
D. Finally, we review the resource inventory to see if the resources are now compliant based on the rules.

Resource Inventory — resources are now compliant
As seen in the image above, the s3 bucket and the EC2 instances are now compliant based on our rules.
Summary
The article provides a step-by-step guide on how to get started with performing compliance check, viewing resource inventory, and fixing configuration issues of non-compliant resources. It discusses the use of AWS Config to perform compliance checks on EC2 instances and S3 buckets.
We have seen that AWS Config is important for compliance, security, and governance on AWS. It helps monitor resource configurations, track changes, and assess compliance against regulatory and industry standards, enabling users to mitigate risks and maintain a secure and compliant cloud environment.
